I was invited to attend the 2015 Digicert Security Summit this week in Las Vegas. For a one day conference it had some really amazing talks by some of the smartest people in the industry.
Gary McGraw gave an amazing talk on security software development life cycle and the Building Security in Maturity Model (BSIMM).
Emily Stark talked about the future of HTTPS everywhere and demoed the new security tab in the developer menu in chrome:

Dan Kaminsky did Dan Kaminsky stuff.

Runa Sandvik gave an amazing humorous, thought provoking and informative talk on protecting press sources on the internet.

Digicert also gave me this iOS controlled drone which seems to be amazingly hackable:

Category: Security
I take a lot of screenshots in OSX (⌘+shift+4) to share and for the longest time I just lived with the 2003-era super cool shadow:

I finally got tired of it and found the solution to turning it off is these two terminal commands:
defaults write com.apple.screencapture disable-shadow -bool true
killall SystemUIServer
Now my screenshots look like this:
 If for some reason you would want to re-live 2003 you can re-enable the drop shadow with these commands:
If for some reason you would want to re-live 2003 you can re-enable the drop shadow with these commands:
defaults write com.apple.screencapture disable-shadow -bool false
killall SystemUIServer
I have been using censys.io a lot lately to do network reconnaissance and noticed they just released a new API that didnt have a CLI frontend so I spent sometime writing a python based one. You can grab a copy here.
Usage is: python censys.py -f (search term)

It is still pretty rough and I will be making more updates as I get time.
Letsencrypt.org is a new project that offers free TLS certificates to allow people to encrypt their traffic.
The project is in a limited beta so I decided that a good test would be to install one of their certificates on to a Nessus scanner I host in AWS.
The install wasn’t complicated and only took about 15 minutes and 9 commands:
cd ~
git clone https://github.com/letsencrypt/letsencrypt
cd letsencrypt
./letsencrypt-auto --agree-dev-preview --server https://acme-v01.api.letsencrypt.org/directory auth
sudo service nessusd stop
sudo cp -i /etc/letsencrypt/live/scan.jerrygamblin.com/fullchain.pem /opt/nessus/com/nessus/CA/servercert.pem
sudo cp -i /etc/letsencrypt/live/scan.jerrygamblin.com/privkey.pem /opt/nessus/var/nessus/CA/serverkey.pem
sudo cp -i /etc/letsencrypt/live/scan.jerrygamblin.com/chain.pem /opt/nessus/com/nessus/CA/cacert.pem
sudo service nessusd start
Now my padlock is green and my traffic is secure:

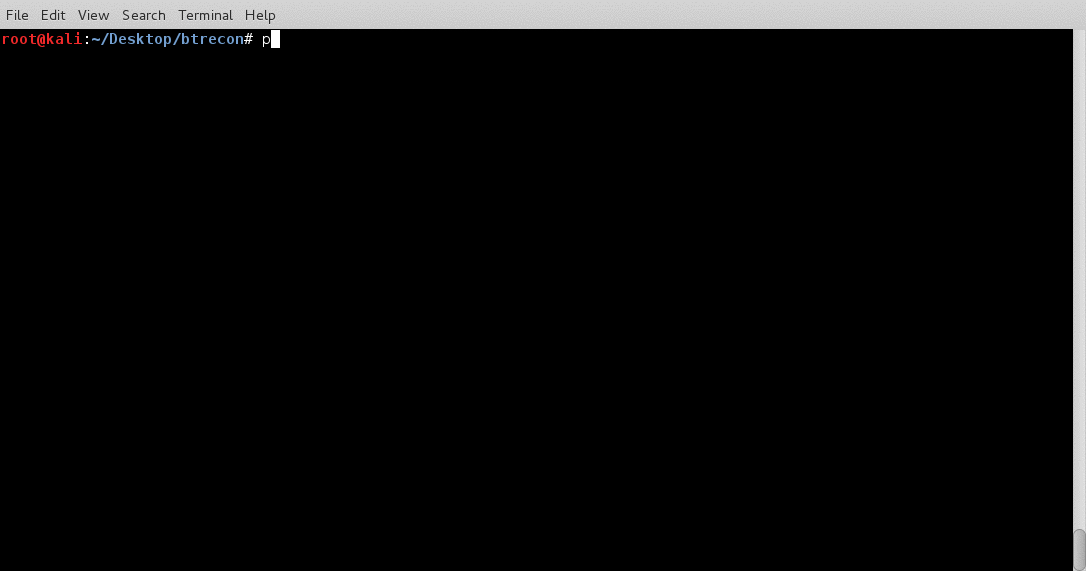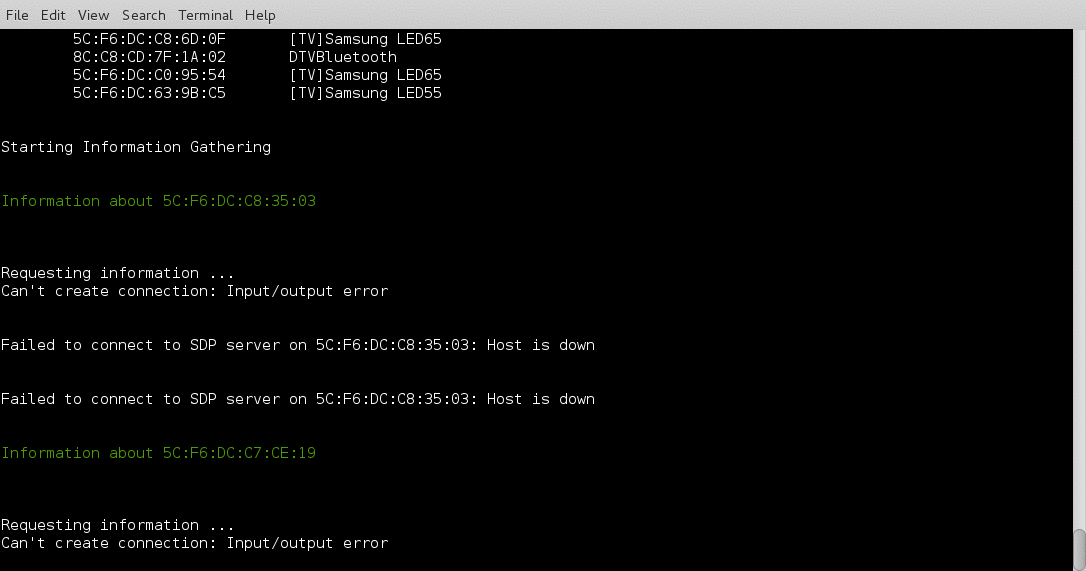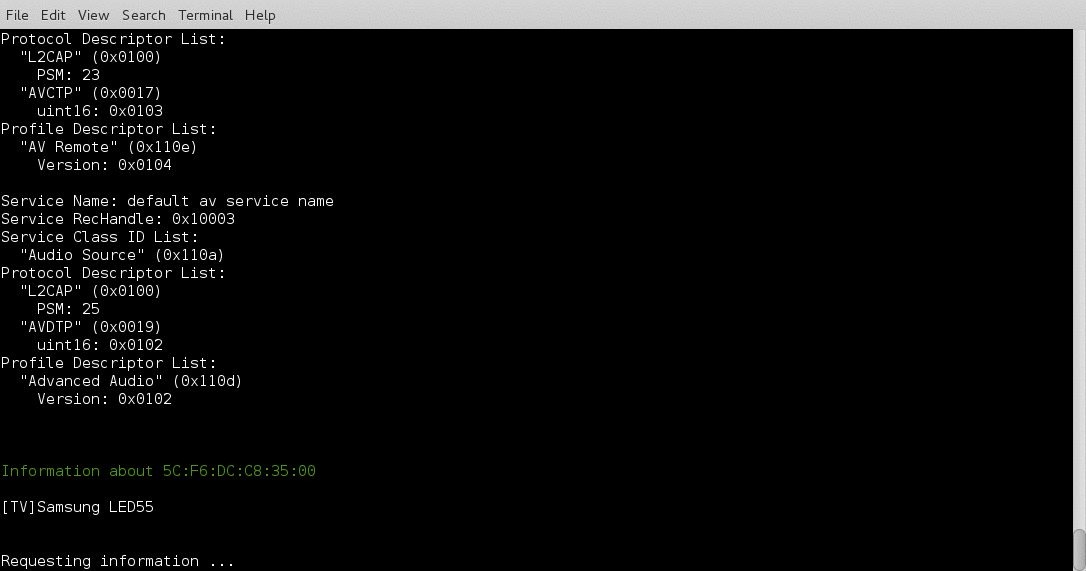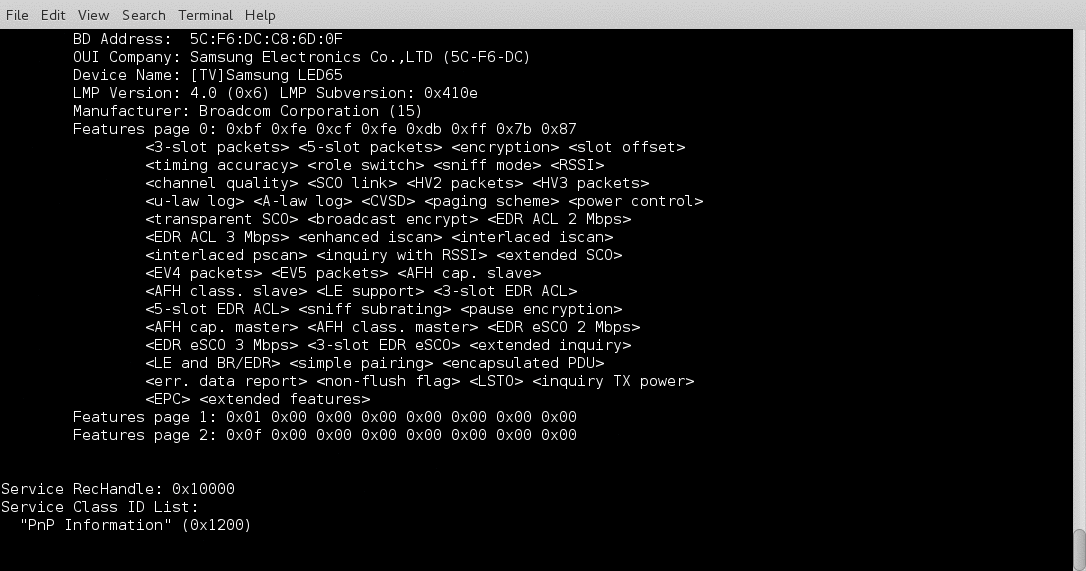
I have been working on a Bluetooth hacking project recently and couldn’t really find a good bluetooth recon tool so I wrote btrecon to do what I need done.
Here is a quick demo:
I still have some work to do on this project as I would like to add some logging and menus but it isnt a bad start. If you have any suggestions or problems please reach out to me on twitter @jgamblin.
I wrote nocommonsssids to quickly remove the top ssids (from wigle.net) from the preferred network list in OSX so that it does not auto connect to them.
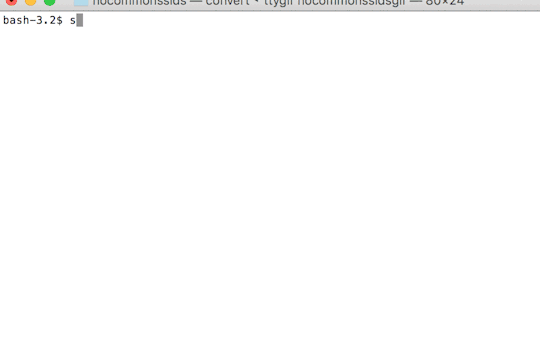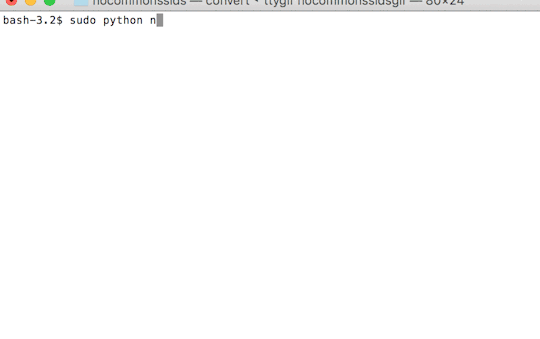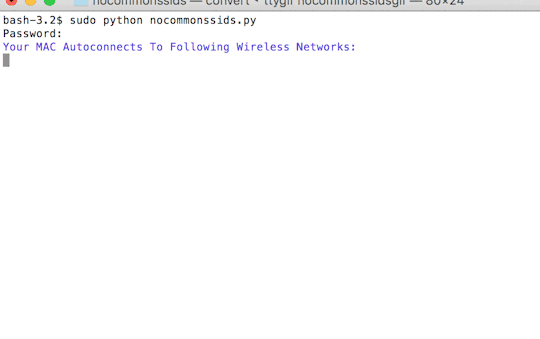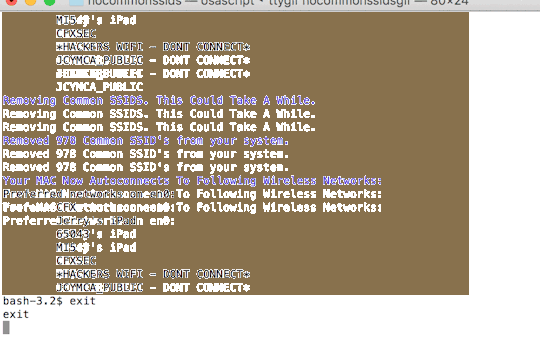
Running this will help stop you from being caught by an EvilAP attack along the line of the Mana Common demo I put together earlier this month. You should also run a VPN anytime you connect to a public wireless network.
I had the opportunity to speak at a “micro- conference” yesterday for the Midwest Cyber Security Alliance with the state auditor Nicole Galloway.
I wanted to use this opportunity to make a bold statement since I knew there would be influential people in the audience who wanted to listen Nicole talk about her new cyber security auditing initiative.
I wrote Mana-Common that builds on Dominic White’s amazing Mana project.
My project used in conjunction with a Ralink 5370 Chipset USB Wireless Card broadcasts 7 of the most popular SSID’s according to wigle.net. Protip: It is easily modified to target smaller audiences who may have saved corporate SSIDs on their devices.
Here is a demo of the terminal output:
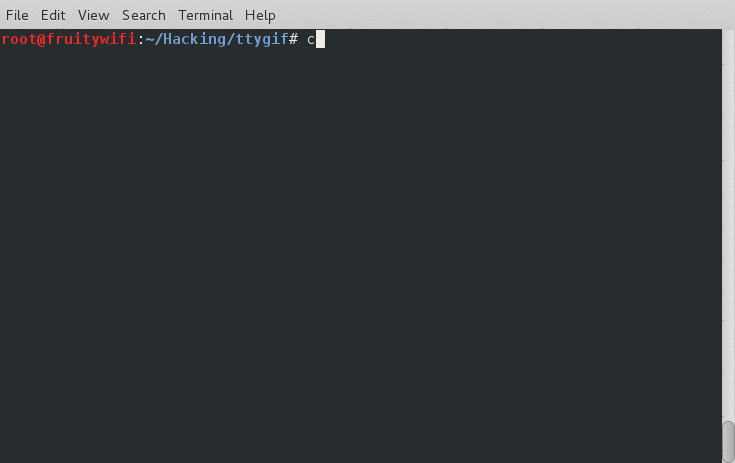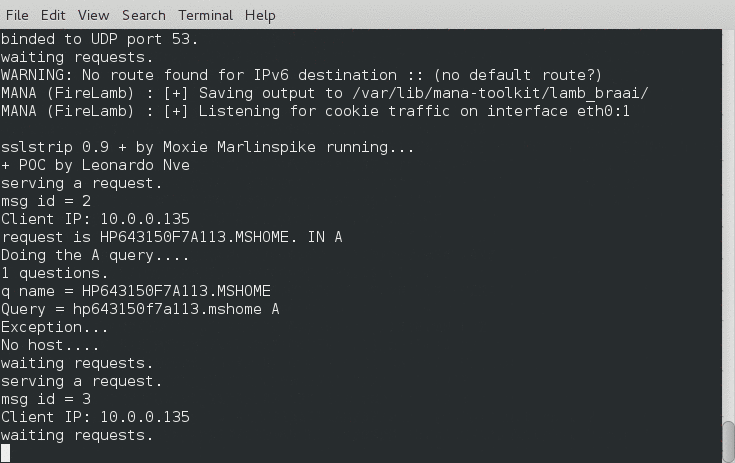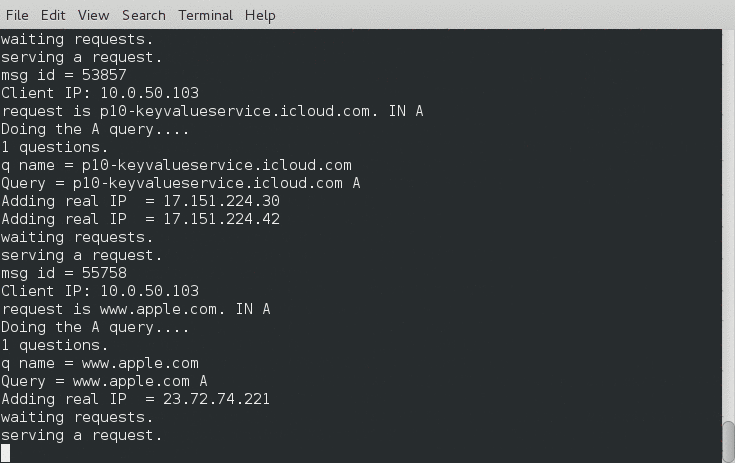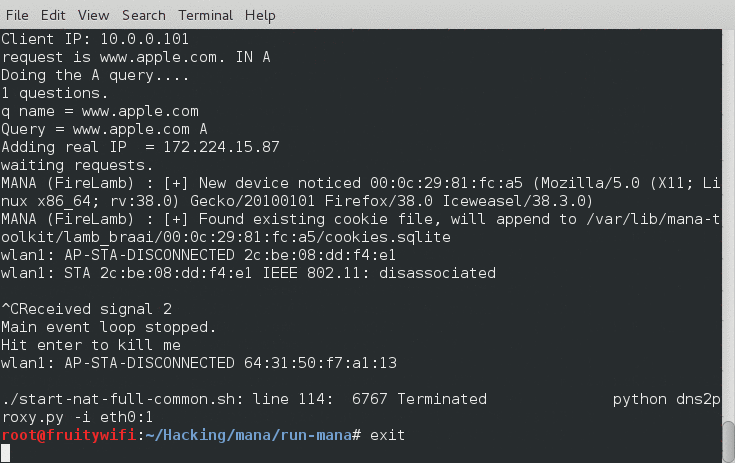
Here is a screenshot of my iPhone picking up the networks:
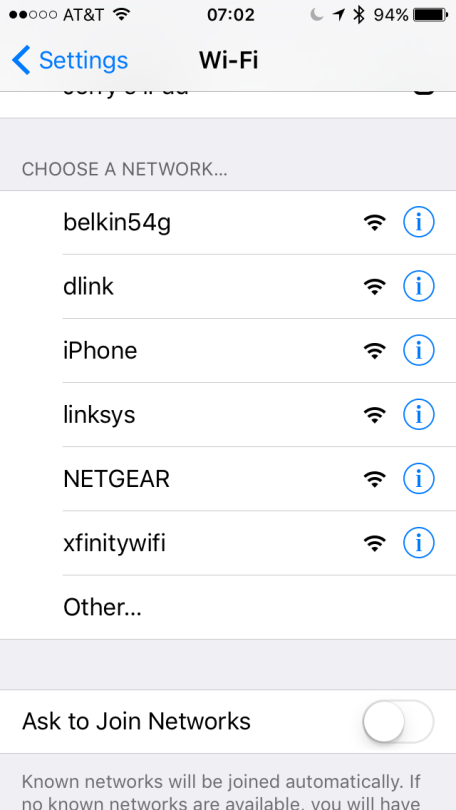
If you have any questions please reach out to me on twitter @jgamblin.
I am getting ready to teach a “Building Your Own Security Lab” series of classes and I really needed a safe place for people to try their hand at wireless hacking.
I built HackAPie that uses a RaspberryPI (this canakit) and openwrt that broadcasts 5 unique wireless networks to crack using tools like wifite and kali.
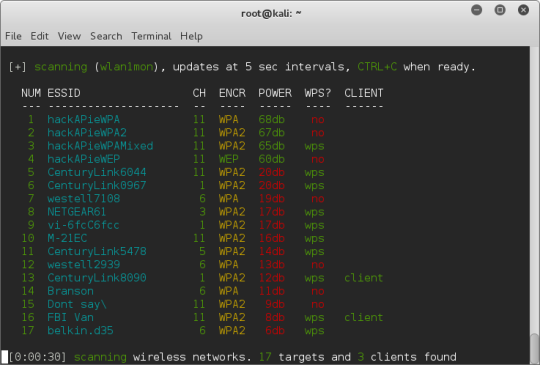
There are still a few bugs to work out but people have asked me if I would share this and I think I have it in a place where I am comfortable doing that. If you have any suggestions or questions please reach out to me at [email protected] or @jgamblin on twitter.
My mentor and I are in the middle of spinning up an information sharing group with local security professionals and next Friday is our first “working session” and we are discussing what building a security lab* looks like and costs.
We really hope to start walking through the tools in future meetings but here is what my security lab build looks like and roughly costs.
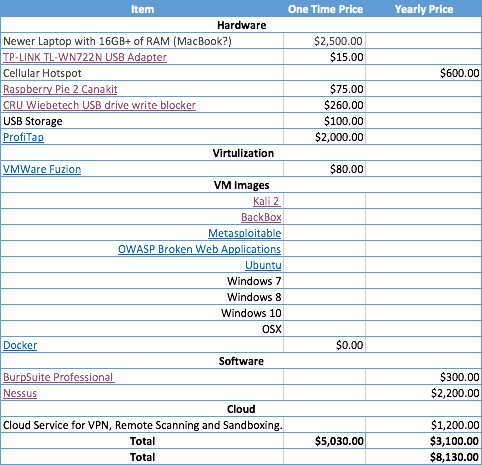
(Not sure why my blog doesn’t like tables. Here is a link to the excel spreadsheet.)
I really hope to pick up some information on what other people have in their labs that I am missing.
*I am not sure if the correct term here is lab, toolkit or security testing platform. You pick.
