I have been to Top Golf for 3 different events this year and was always amazed by their RFID technology and have always left wondering “What is in a Top Golf golfball?”.
So when I saw a few “Top Golf” golf balls in the $1 ball bin at a golf store I bought them and decided to answer that question.





That little “passive EPC Gen 2 ultrahigh-frequency (UHF) RFID” tag is what makes TopGolf so awesome. Now all I need to do is invest in a UHF RFID reader to see what is actually on the tag.
Protip: Sawing a golf ball in half is a lot harder than it sounds.
Category: Hacking
I have become more and more interested in hardware security lately and while I have been having a lot of fun learning about RFID Security I knew the next logical step would be to try to learn how to use a software-defined radio.
After doing a lot of reading and research over the last couple of weeks I came to learn that the best way to learn SDR is with a ~$20 HD DVB-T from Realtek called the RTL2832U.
The RTL-SDR blog sells an “upgraded” RTL-SDR on Amazon for $25 that I picked up and really like.

Some of the projects I have started to explore include:
Tracking Airplanes Using Dump1090:

Decoding and Tracking TPMS:

RTLSDR-Scanner for general scanning:

I have a lot more to learn with this setup but I can easily see that this will quickly turn me into dropping a few hundred dollars into a HackRF so that I can transmit as well as receive.
From time to time I have the need to test or verify a web application vulnerability through the TOR network using BurpSuite. The easiest way to do this to use the pre-bundled TOR Browser.
Configuration is fairly easy:
- Download, Install and Start the TOR Browser:

- Verify that the SOCKS proxy is started on 127.0.0.1:9150

- Configure Burp (Options > Connections > Upstream Proxy Servers)

- Then…

(Legally with proper permission of course!)
Pro Tips:
TorBrowser has to stay running while using Burp.
Verify the Proxy is still active if you have to restart Burp.
The TOR network runs slow sometimes.
Some web hosts block TOR traffic.
Dry clean only.
On Wednesday night I tweeted this:
If you are using TrueCrypt you should stop. Hashcat is now optimized to crack TrueCrypt volumes. https://t.co/voBdtKuuHW
— Jerry Gamblin (@JGamblin) December 10, 2015
I started getting retweets and replies like this on Friday from people I respect (and a bunch from people I don’t know):
@JGamblin this is a non sequitur. there are valid reasons to stop using TC, but Hashcat isn't one of them.
— Kyle Maxwell (@kylemaxwell) December 11, 2015
https://twitter.com/averagesecguy/status/674768017864134657
So people REALLY like TrueCrypt or I didn’t make my point articulately enough. In case I didnt make my point well enough I will try to lay it out here.
3 Reasons Why I Think You Should Stop Using TrueCrypt:
The developer stopped maintaining it, took down the webpage and replaced it with this.
“WARNING: Using TrueCrypt is not secure as it may contain unfixed security issues“.

I think that this reason should be more than enough to get 99% of people to stop using it.
The latest version of HashCat includes support for TrueCrypt volumes.
If you are using good passphrases (most people don’t) it really isnt a big deal but it does lower the level of complexity for hacking a TrueCrypt volume with a weak password from a medium-high skill level (Think Security Professional) to downloading kali and following instructions (Think Help Desk Analyst).
The developer stopped maintaining it, took down the webpage and replaced it with this.
“WARNING: Using TrueCrypt is not secure as it may contain unfixed security issues“.

There are many other open source and paid alternatives that you can evaluate and pick the best one for you. So unless you have an amazingly valid reason to not move off of TrueCrypt you should move off it as soon as possible.
HID proximity cards encode a facility code and internal card number in hex on most cards. Decoding it is extremely easy and should take less than a minute.
Equipent Needed:
Omnikey Reader (I like the 5025CL)
RFIDIOT
BRIVO Card Calculator
Steps:
Run isotype.py from the RFIDIot tool kit and copy the ID:

Past the ID into the BRIVO decoder:

It is really that simple. A made a quick video demo (that is tinted purple for some reason):
I have some writeable HID proximity cards on the way and will have a blog up soon on how to completely clone one.
As part of my research into RFID security I came across the “EM4100 RFID Cloner kit” by KBEmbedded which outside of having a terrible name is an amazing low-frequency (125 kHz) self-contained RFID cloner that can store and replay 16 cards.

I was lucky enough to be in the Portland area this week and be able to have dinner with Kris Bahnsen who designed the board and he said the that he thinks he could rewrite the software to read and replay HID proximity cards which would make this a must have gadget for all security professionals.
As it stands now this is an awesome $25 tool that is amazingly fun to play with and you should order one!
I have recently started investigating RFID security and picked up a Chameleon Mini. It is an amazing project with a ton of potential. In these quick demo videos I will show how to clone the UID of both a Mifare 1K 4B card and a Mifare 1K 7B card using the Chameleon.
Cloning the Mifare 1K UID (Aria Card):
Cloning the Mifare 1K 7B UID (Oyster Card):
These were both extremely simple to do. In the future I will be demoing how to take full card dumps from an RFID card and load it on to the Chameleon Mini for a “true clone”.
Tool List:
ACR122U
ChamelemonMini
ZTerm
LibNFC
Cardpeek
Oyster Card
Aria Card
Hardware Picture:

Disclaimer: While cloning the UID isnt a full spoof of the card WAY (READ:MOST) more organizations rely on UID based authentication then should. While the tools say the UIDs have been cloned I have not tested these on any live systems and would not without permission.
I was invited to attend the 2015 Digicert Security Summit this week in Las Vegas. For a one day conference it had some really amazing talks by some of the smartest people in the industry.
Gary McGraw gave an amazing talk on security software development life cycle and the Building Security in Maturity Model (BSIMM).
Emily Stark talked about the future of HTTPS everywhere and demoed the new security tab in the developer menu in chrome:

Dan Kaminsky did Dan Kaminsky stuff.

Runa Sandvik gave an amazing humorous, thought provoking and informative talk on protecting press sources on the internet.

Digicert also gave me this iOS controlled drone which seems to be amazingly hackable:

I have been working on a Bluetooth hacking project recently and couldn’t really find a good bluetooth recon tool so I wrote btrecon to do what I need done.
Here is a quick demo:
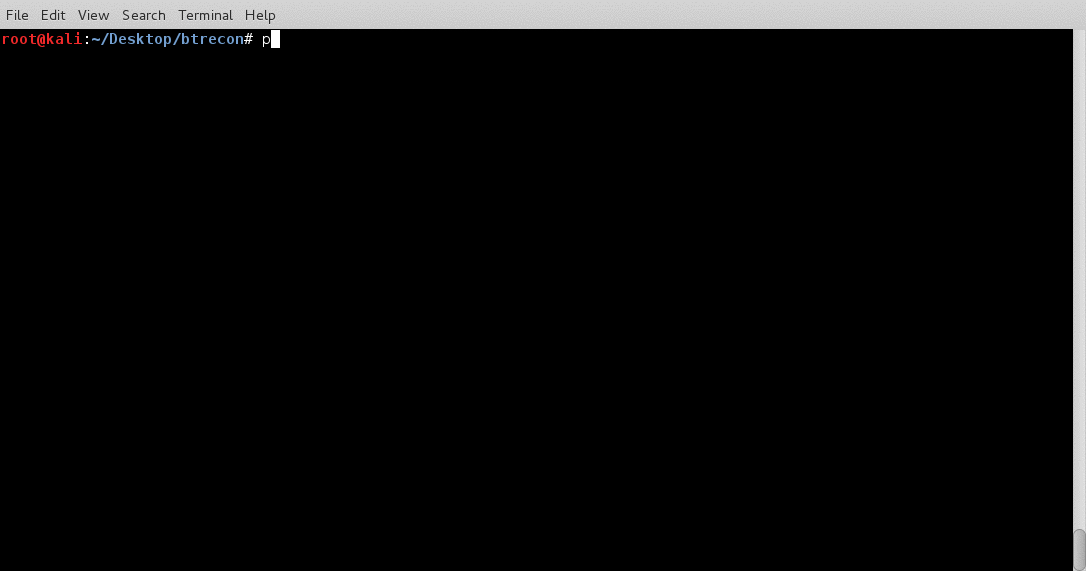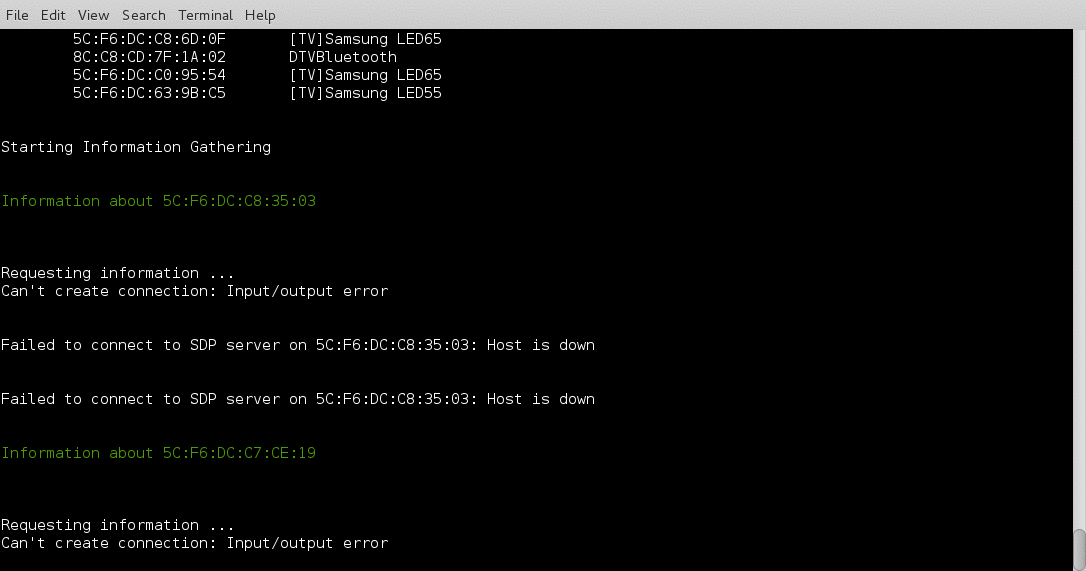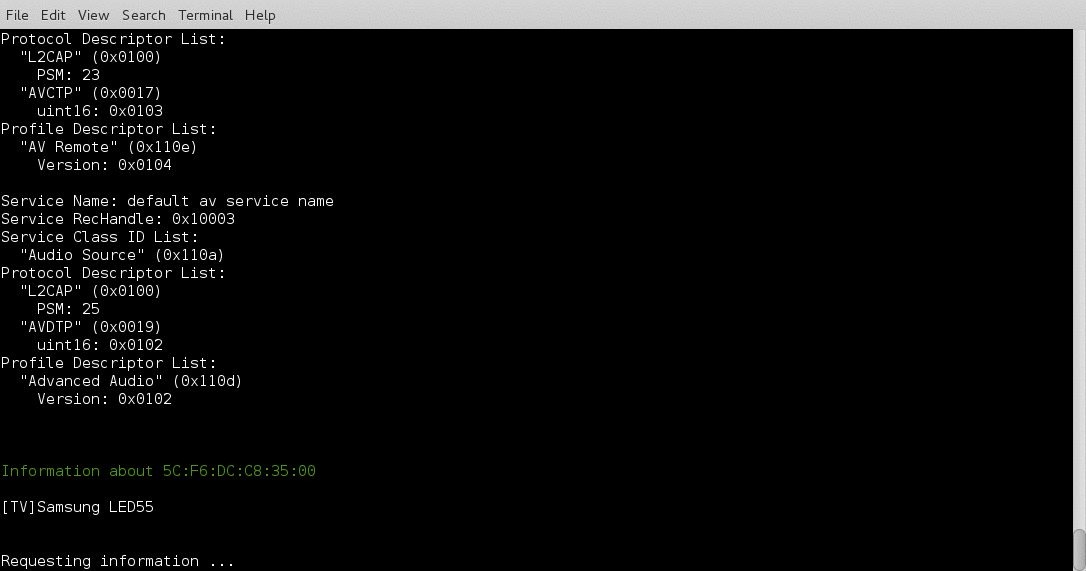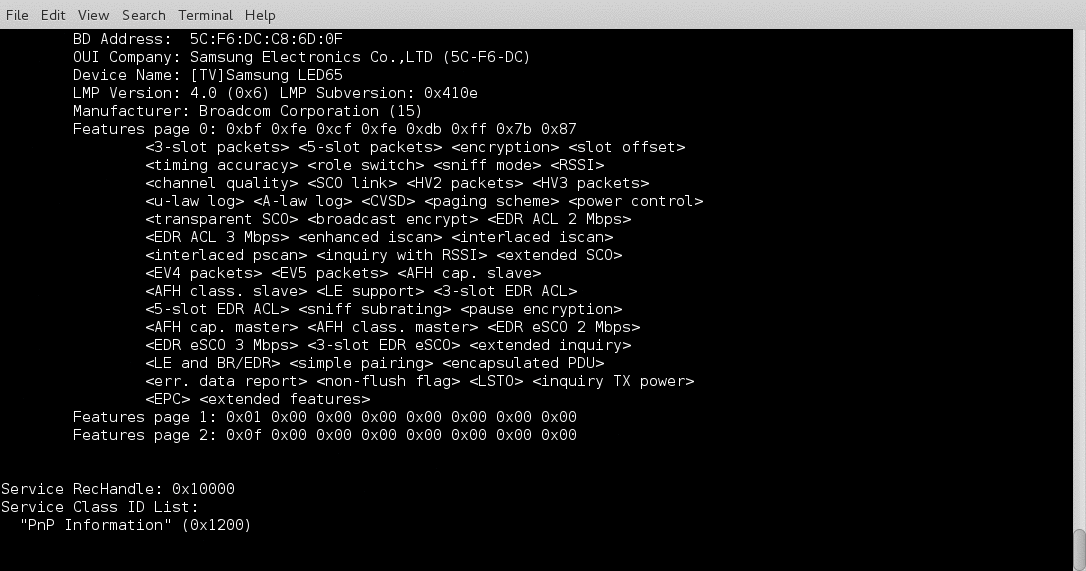
I still have some work to do on this project as I would like to add some logging and menus but it isnt a bad start. If you have any suggestions or problems please reach out to me on twitter @jgamblin.